Introduction to Cyber Threat Intelligence
This section will be an introduction to cyber threat intelligence.
Table of Contents
- Introduction
- Cyber Threat Intelligence Life Cycle
- Planning and Direction
- Collection
- Processing
- Analysis
- Dissemination
- Feedback
- CTI Standards and Frameworks
- CTI Tools
- urlscan.io
- abuse.ch
- PhishTool
- Cisco Talos
Introduction
Threat Intelligence (TI) or Cyber Threat Intelligence (CTI) can be defined as evidence-based knowledge about adversaries. This includes their indicators, tactics, motivation, and actionable advice against them. These information can be used to protect assets.
The following table will cover some common terms.
| Term | Description |
|---|---|
| Data | Discrete indicators associated with the adversary (e.g. IP addresses, hashes, URLs, domain names, etc.). |
| Information | A combination multiple data points that answers questions (e.g. How many failed login attempts occurred?). |
| Intelligence | The correlation of data and information to extract patterns of actions based on contextual analysis. |
The primary goal of CTI is to understand the relationship between your operational environment and the adversary and how to defend the environment from any attacks.
To achieve the goal, we can develop the cyber threat context by answering some of the following questions:
- Who is the adversary/attacking you?
- What are their motivations?
- What are their capabilities?
- What artefacts and and indicators of compromise (IOC) should we look out for?
To answer the above questions, threat intelligence can be gathered from different sources:
- Internal
- Corporate security events such as vulnerability assessments and incident response reports.
- System logs and events
- Awareness training reports
- Community
- Forums
- Dark web communities for cybercriminals (e.g. forums)
- External
- Threat intel feed
- Online marketplaces
- Public sources such as government data, publications, social media, etc.
We can break down threat intel into the following classifications:
| Classification | Description |
|---|---|
| Strategic Intel | High-level intel that looks into the organisation's threat landscape and maps out the risk areas based on trends, patterns, and emerging threats that may impact business decisions. |
| Technical Intel | Evidence and artefacts of attack used by an adversary. Incident response teams can use this intel to create a baseline attack surface to analyse and develop defence mechanisms. |
| Tactical Intel | Assesses the adversaries' TTPs to strengthen security controls and address vulnerabilities through real-time investigations. |
| Operational Intel | Looks into an adversary's specific motives and intent to perform an attack. Security teams can use this intel to understand critical assets in the organisation that may be targeted. |
By answering the questions using sources from various points and classifying threat intelligence, we can identify and respond to threats better.
Cyber Threat Intelligence Life Cycle
Threat intel is obtained from a data-churning process that transforms raw data into contextualised and action-oriented insights data that can then be used to triage incidents, develop tactics, and strengthen defences.
There are 6 phases in the CTI life cycle:
- Planning and Direction
- Collection
- Processing
- Analysis
- Dissemination
- Feedback
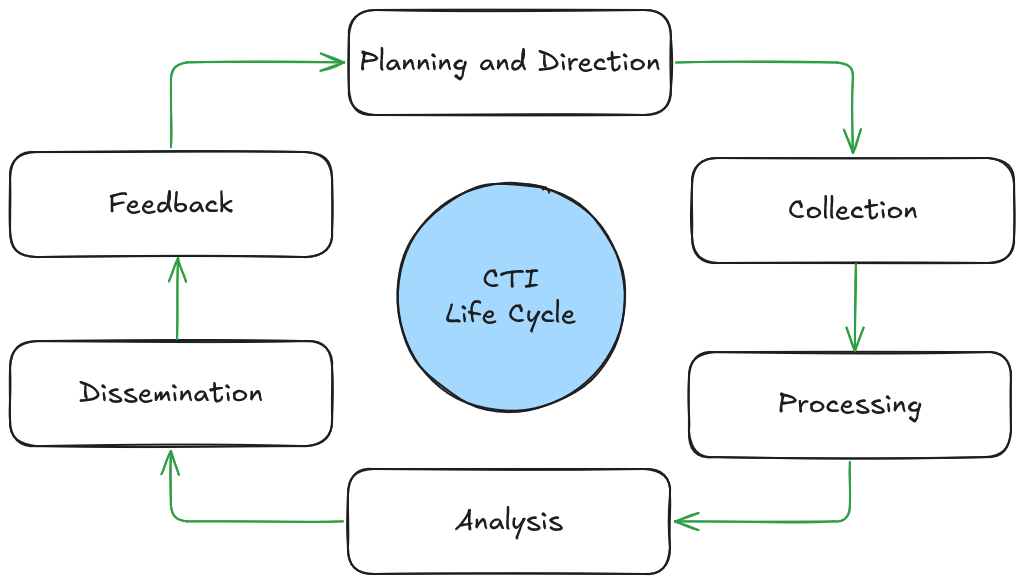
Planning and Direction
This phase is where the objectives and goals are defined for the threat intel program.
This phase also involves identifying the following:
- Information assets and business processes that require defending.
- Potential impact or disruptions on losing the assets.
- Sources of data and intel to be used towards protection.
- Tools and resources required to defend the assets.
This phase also allows security analyst to define the questions to investigate incidents.
Collection
Once the objectives have been defined, we will need to gather the required data to address them. The data obtained can be from different sources such as commercial, private, and open-source resources.
Processing
After the data have been collected such as raw logs, vulnerability information, malware information, network traffic, and more, we can process the data to ensure that it is extracted, sorted, organised, and correlated with the appropriate information and tags.
This phase is where the data is aggerated so that it is in a standard format and will make sense to the analyst or security personnel reading it.
Analysis
Once the data has been aggregated (processed), security personnel (i.e. analysts) can derive insights.
The decisions make here includes:
- Investigating a potential threat through uncovering indicators and attack patterns.
- Defining a playbook or action plan to avert or defend against an attack.
- Strengthening security controls or implementing new controls.
Dissemination
This phase is where different stakeholders consume the intelligence in varying languages and formats.
An example will be where C-suite members will want a concise, high level report covering the trends in adversarial activities while technical teams will want information such as IOCs, TTPs, and action plans/playbooks.
Feedback
As analysts rely on the responses provided by stakeholders to improve the threat intel process, feedback should be regularly provided on items such as ways to improve or areas to focus on.
Feedback allows technical teams to improve the threat intel process and implementation of any security controls.
CTI Standards and Frameworks
Standards and frameworks provides structure to rationalise the distribution and use of threat intel across industries.
The following are some useful or common standards and frameworks:
- MITRE ATT&CK
- TAXII - https://oasis-open.github.io/cti-documentation/taxii/intro
- STIX - https://oasis-open.github.io/cti-documentation/stix/intro
- Cyber Kill Chain
- The Diamond Model
The MITRE ATT&CK framework is a knowledge base of adversary behaviour. It focuses on the indicators and tactics. Analysts can use this information when investigating and tracking adversarial behaviour.
The Trusted Automated eXchange of Indicator Information (TAXII) defines protocols for securely exchanging threat intel to have near real-time detection, prevention, and mitigation of threats.
The protocol supports two sharing models:
- Collection - Threat intel is collected and hosted by a producer upon request by users using a request-response model.
- Channel - Threat intel is pushed to users from a central server through a publish-subscribe model.
Structured Threat Information Expression (STIX) is a language and serialization format developed to exchange CTI information. STIX provides defined relationships between sets of threat information such as observables, indicators, adversary TTPs, attack campaigns, and more.
CTI Tools
The following are some tools that we can use to gather CTI:
- urlscan.io - https://urlscan.io/
- abuse.ch - https://abuse.ch/
- PhishTool - https://www.phishtool.com/
- Cisco Talos - https://talosintelligence.com/
urlscan.io
This is a free service that has been developed to assist in scanning and analysing websites. It is used to automate the process of browsing and crawling through websites to record activities and interactions.
When a URL is submitted, information such as the domains, IP addresses, requested resources, a snapshot of the web page, technologies used, and more are recorded.
| Tab | Description |
|---|---|
| Summary | Provides general information about the URL such as the IP address and domain details. |
| HTTP | Provides information on the HTTP connections made by the scanner to the site. |
| Redirects | Displays any identified HTTP and client-side redirects on the site. |
| Links | Displays all identified links outgoing from the site's homepage. |
| Behaviour | Provides details of variables and cookies found. These may be useful in identifying the frameworks used when developing the site. |
| Indicators | Lists all IP addresses, domains, and hashes associated with the site. The indicators do not imply any malicious activity related to the site. |
Due to the dynamic nature of internet activities, the results may differ depending on when the analysis was performed.
abuse.ch
ABUSE.ch is a research project hosted by the Institute for Cybersecurity and Engineering at the Bern University of Applied Sciences in Switzerland.
It was developed to identify and track malware and botnets through several operational platforms developed under the project:
- MalwareBazaar - A database used for sharing malware samples.
- Feodo Tracker - A platform used to track botnet C2 infrastructure linked with Emotet, Dridex, and TrickBot.
- SSL Blacklist - A resource for collecting and providing a blocklist for malicious SSL certificates and JA3/JA3s fingerprints.
- URLhaus - A database used for sharing malicious URLs that are being used to distribute malware.
- ThreatFox - A platform for sharing indicators of compromise (IOCs).
MalwareBazaar - https://bazaar.abuse.ch/
Feodo Tracker - https://feodotracker.abuse.ch/
SSL Blacklist - https://sslbl.abuse.ch/
URLhaus - https://urlhaus.abuse.ch/
ThreatFox - https://threatfox.abuse.ch/
PhishTool
PhishTool can be used to perform email analysis and uncover email IOCs, potentially prevent and perform forensic analysis on emails. PhishTool has two versions - Community and Enterprise. This section will focus on the Community version features.
https://www.phishtool.com/
The following are some core features:
- Perform email analysis
- Heuristic intelligence
- Classification and reporting
When opening PhishTool, we are presented with the following screen with some tabs:
- Analysis - Allows us to view information on the selected email.
- History - Lists all submissions made with their resolutions.
- In-tray - An enterprise feature to receive and process phish reports by integrating platforms such as Google Workspace or Microsoft 365.
By uploading an email (usually .eml) file, we are able to see information such as the headers, received lines, X-headers, security such as DMARC, DKIM, and SPF, attachments, message URLs, and more.
Cisco Talos
Cisco Talos provides actionable intelligence, visibility on indicators, and protection against emerging threats by collecting and analysing data from their products.
https://talosintelligence.com/
We are able to see information such as email and spam trends or search for IP and domain reputation. Additionally, if we are investigating a file, can enter information such as the file hash.
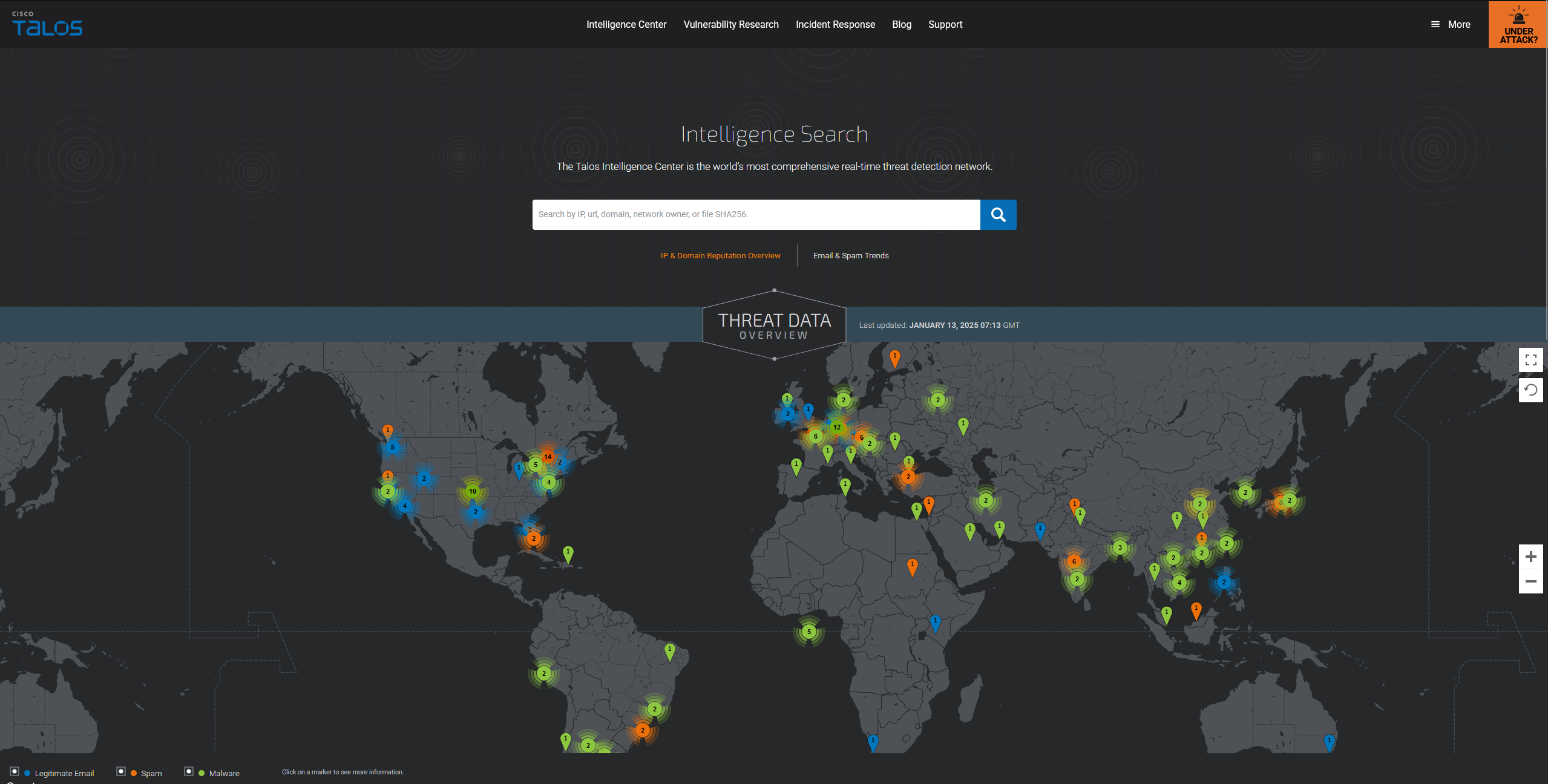
Other tabs include Vulnerability Research, where we can view disclosed vulnerability reports and more.